The head of the government’s cyber response unit says 80% of reported cyber-attacks could be avoided if New Zealanders and businesses improved their passwords, used two-factor authentication, updated device software, and updated device and software privacy settings.
The computer emergency response team (Cert NZ), a division of the Ministry of Business, Innovation, and Employment (MBIE), said in Q3 2021 it received 2,072 reports of cyber-attacks, a figure up 53% from 1,351 in Q2.
But Cert NZ director Rob Pope told BusinessDesk that number “underrepresented” the scale of cyber-attacks against New Zealanders and businesses.
Cert reported $3.3 million in loss during the quarter to the affected people and businesses, though this was down from $3.9m in Q2. The figure in Q3 2020 was $6.4m.
A 73% increase from Q2 in reports of phishing and credential harvesting was attributed to the FluBot malware scam that targeted Android devices via text messages.
151 reported malware attacks were up from 32 in Q2.
“The main aim of the game is to lift the cyber resilience of the whole country and the only way we can do that is when we know what we’re actually dealing with,” Pope said of the importance of people reporting.
He said the technology used in cyber-attacks was complex, but that Cert’s simplistic advice was the most important in protecting both financial welfare and data.
“When we boil it down, despite the sophisticated approaches that these attackers are adopting, and continually evolving on … the relatively simplistic advice we're offering is, in fact, the most important in actually protecting both your financial welfare and your data.”
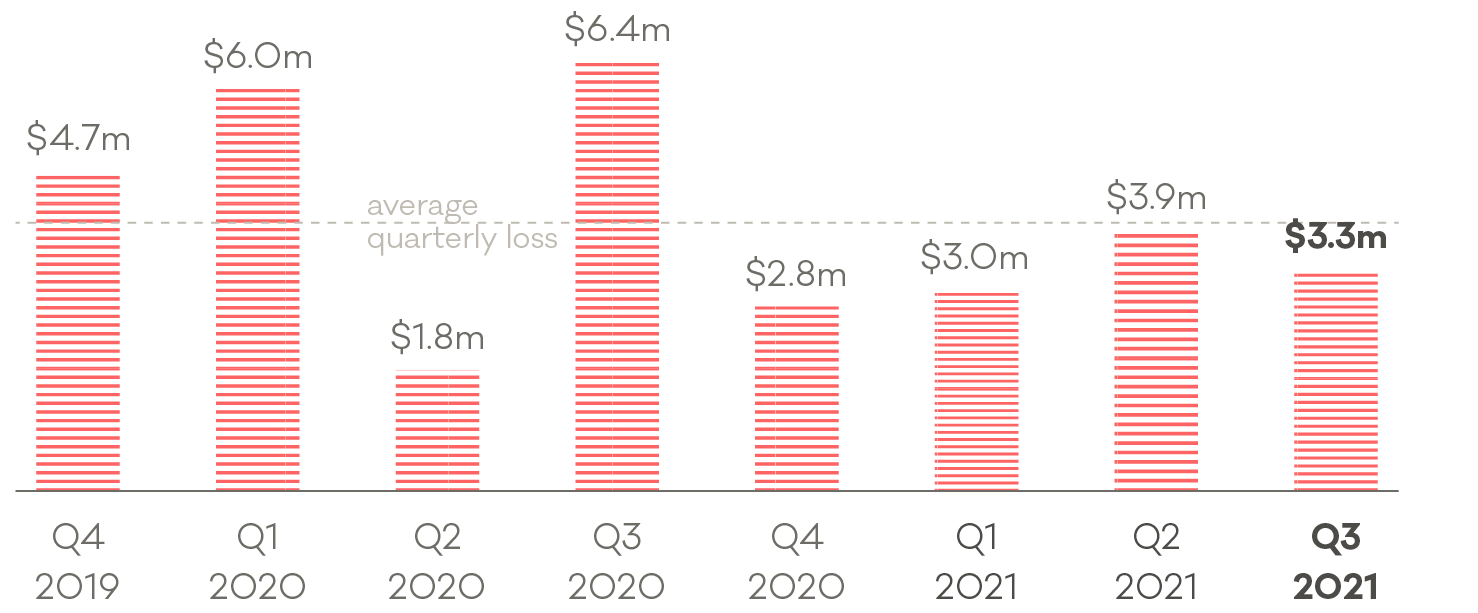 Direct financial losses reported to Cert NZ. (Image: Cert NZ)
Direct financial losses reported to Cert NZ. (Image: Cert NZ)Cert’s primary advice to all is to change passwords to be unique and stronger, use two-factor authentication for more secure login and identification verification, and update software and privacy settings.
60% of Q3’s reported incidents were from individuals, 15% from businesses and about 20% were anonymous, likely from businesses who for commercial reasons did not want to disclose sensitive information.
Pope said the differences in reported figures every quarter showed the incidents don’t reflect the true volume of cyber incidents in Aotearoa.
“It’s mainly about keeping our eye on the ball … If we don’t know, we can’t help and it’s a bit of a chicken and egg situation.”
“Common sense says that the more that reports are being provided to us, it shows that while there might be a greater awareness and willingness to report, it does reflect the quite significant number of attacks that are occurring, which aren't being reported.”
He said if individuals or businesses reported incidents to Cert as soon as possible, it will mean the organisation can help with things like recovery of funds or minimising technical compromises.
But with fluctuations in the reported numbers, Cert’s quarterly reports make it difficult to distinguish whether it is reporting or incidents, or both, that are on the up.
Lay of the land
Public awareness of cyber-attacks in NZ likely rose during 2021 with high profile data breaches against the Reserve Bank and Waikato DHB, and the system disruption to multiple organisations in such as Kiwibank, ANZ, and NZ Post in September and October following unconfirmed reports of a distributed denial of service (DDoS) attacks.
None of the organisations confirmed they were victims of cybercrime at the time, and it was Cert that tweeted it was aware of a DDoS attack targeting NZ firms.
“Quite often some of these high-profile incidents that have been reported lately have broader impacts. So, we, by understanding that, we also foot it by trying to prevent further spread of that by notifying other organisations that could be vulnerable to a particular sort of an attack.”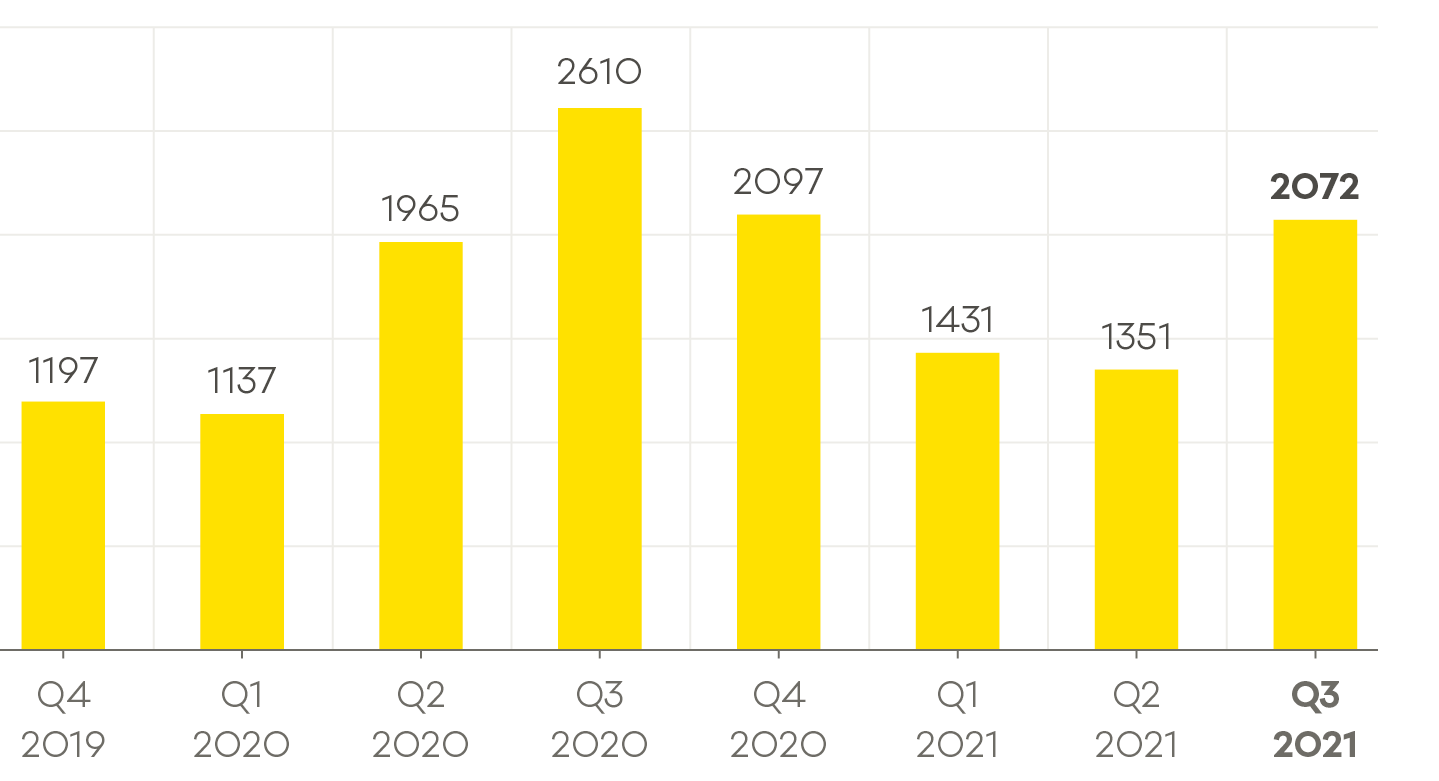 Incidents responded to by Cert NZ. (Image: Cert NZ)
Incidents responded to by Cert NZ. (Image: Cert NZ)
Cert works closely with organisations and partners to help people when they are under attack to respond as quickly as possible. This could be an individual accidentally answering a dodgy email right up to an organisation losing confidential data to hackers.
It also works with internet service providers (ISPs) to identify traffic affecting the organisation and advise on how to “fill any gaps that might actually be present in their system”.
Pope said simple cyber housekeeping could be enough to protect many New Zealanders, and that spending on new technology to fight the threat was a “sliding scale”.
“There's no way that you would expect a small business in New Zealand to invest at the level of the major corporates,” he said.
“One, it’s not necessary, but secondly, it’s important that they are aware of what cybersecurity they need to actually put in place to secure their livelihoods and their commercial viability.”
Cyber spend
MBIE financials show Cert NZ’s 2020/2021 budget was $8.1m. It also is allocated a further $217,000 from the Ministry of Foreign Affairs and Trade for Pacific cybersecurity initiatives.
Cert currently employs 33 people across incident response, communications, engagement, and data teams.
Pope said he believed the organisation was spending its annual budget effectively across the three service delivery areas of response, engagement, and website.
“Everybody says, ‘give us more money, we do more things.’
“The investment we have, we cut our cloth accordingly to provide as much service as we can to New Zealanders and to businesses and cut across those three areas.
“We've got a sound foundation, we're very comfortable that we pitch their services in the right areas. Better investment would result in more scaling,” Pope said.
With a small team and only some employees dedicated to real-time response to ongoing cyber-attacks, Cert’s concentration will continue to be on preventative education.
Its response team provides technical support and analysis to affected parties, while its engagement team works with partner agencies to monitor intelligence feeds, and on awareness campaigns including Cert’s Cyber Smart Week, which was in October.